Phishing scams have become more sophisticated, making them harder to detect and more effective at targeting individuals and businesses. Scammers take advantage of the way we conduct our daily activities online, using deceptive tactics to gain access to personal and financial information. In this article, we’ll explain common phishing scams, share real-life examples, and provide practical tips to help you recognize and avoid them.
Common Phishing Scams
Phishing is a fraudulent attempt to steal personal or financial information by pretending to be a trusted source. Scammers often use emails, text messages, or fake websites to trick individuals into clicking malicious links, downloading harmful attachments, or revealing sensitive data. Below are some of the most common phishing scams to watch out for.
Email Phishing
Email phishing is one of the most common scams. Attackers send fraudulent emails that appear to come from trusted sources, aiming to steal personal information or install malware. These messages often use urgency or fear to prompt clicks on malicious links or attachments, such as fake coupons, gift card offers, or payment requests. Opening them can expose your data or compromise your device.
Vishing (Voice Phishing)
Vishing is phishing conducted over the phone. Scammers pose as bank representatives, government officials, or law enforcement officers, using intimidation or confusion to pressure victims into sharing financial details, Social Security numbers, or making payments. These calls often create a false sense of urgency, warning of fraudulent activity, overdue taxes, or frozen accounts to influence the recipient into taking action.
Smishing (SMS Phishing)
Smishing scams come through text messages (SMS), often posing as banks, delivery services, or prize alerts. Messages include malicious links that prompt recipients to claim a prize, apply for a fake job, verify an account, or download harmful software. The personal nature of texts makes these scams easier to fall for.
Angler Phishing
Angler phishing uses fake social media accounts posing as popular brands or customer service teams. Scammers use offers of support, promotions, or urgent warnings to lure people into providing personal information or clicking a malicious link.
Website Spoofing
Website spoofing is a form of phishing where scammers create fake websites that closely mimic legitimate ones. These fraudulent sites often use deceptive domain names—sometimes just one letter or character off from the real site—to trick users into thinking they're on a trusted platform.
Often tied to online shopping scams or account logins, spoofed websites are designed to steal login credentials, credit card numbers, and other sensitive personal information. Once a user enters their details, the information is harvested and can be used for identity theft or financial fraud.
Real Life Examples of Scams
Phishing scams happen every day, and even if you haven’t encountered one, you likely know someone who has.
Here are a few real-life examples:
“Amazon (supposedly) texted to inform me there was a problem with my order, directing me to click a link to rectify the situation. The problem: I hadn’t ordered anything. But I can see where people might fall for that!”
Here’s a common toll-related smishing scam that people have been receiving all across the county recently:
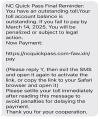
Here’s someone discussing a common vishing scam:
“I get a call on my cell phone from a local number I don’t recognize so I ignore it. Caller leaves a voicemail which I listen to: supposedly Comcast Xfinity saying I’m going to lose my 50% current discount at midnight tonight unless I call that number back.”
And here’s another common smishing example, that’s one of those “too-good-to-be-true” job offers:
How To Prevent Phishing Scams
Phishing scams are constantly evolving, making it essential to stay vigilant and take proactive measures to protect your personal and financial information. While email spam filters can block some phishing attempts, scammers are always finding new ways to bypass security measures. Here are some steps you can take to reduce your risk of falling victim to phishing scams.
Use Security Software
Installing antivirus software, firewalls, and anti-phishing tools can help detect and block malicious emails and websites. Programs like Norton, McAfee, and Bitdefender offer phishing protection by flagging suspicious links and attachments. Keep your software updated automatically to defend against the latest threats.
Stay Alert for Red Flags
Phishing attempts often contain subtle warning signs, such as:
- Misspellings and grammatical errors in emails or messages
- Unfamiliar senders or suspicious-looking email addresses
- Urgent requests for personal information
- Too-good-to-be-true offers
If something seems off, do not click links, open attachments, or share sensitive information.
Verify Before You Act
If you receive an unexpected message—whether by email, text, or social media—take a moment to pause before clicking any links or responding. Even messages that appear to come from trusted companies, like Amazon or your bank, can be designed to look legitimate in order to entice you into sharing personal information or visiting a harmful website.
When in doubt, don’t click. Instead, go directly to the company’s official website or use their verified customer service number to confirm whether the message is real. Avoid using the contact information or links provided in the suspicious message, as these may lead you straight to a scam.

